一、前言
Openldap为啥要加密
Openldap默认使用简单验证,对slapd的所有访问都使用明文密码通过未加密通道进行。为了确保信息安全,需要对信息进行加密传输,SSL(Secure Sockets Layer)是一个可靠的解决方案。
它使用X.509证书,由可信任第三方(Certificate Authority(CA))进行数字签名的一个标准格式的数据。有效的数字签名意味着已签名的数据没有被篡改。如果签名的数据被更改,将不会通过验证。
SSL/TLS加密原理简介
SSL/TLS是基于PKI机制的加密方式,包括证书认证、密钥交换、非对称加密、对称加密。SSL/TLS采用CA作为服务端核客户端都信赖的具有权威性的组织,证书的颁发和认证都依赖于CA,并假定CA颁发的证书是可靠的、可信赖的,证书里面的内容是真实的、有效的,并可用于客户机和服务器进行安全的可靠的通信加密。
SSL/TLS证书用来认证服务器和客户机双方的身份,并用于密钥交换的非对称加密。密钥交换完毕之后,就可以用这个密钥做通信数据的对称加密了,具体的加密算法是由客户机和服务器相互协商得来的。服务器和客户机由于SSL/TLS库的不同以及用户的配置不同,双方支持的算法列表不完全相同,当双方做SSL/TLS握手的时候,就需要将自己支持的算法列表以及优先顺序告知对方,一旦对方按照优先顺序找到了第一个支持的算法,那么协商完成,否则双方协商失败,SSL/TLS连接断开。
二、自生成证书
2.1 自建 CA 中心
2.1.1 CA中心生成自身私钥
1 | [root@localhost openldap]# cd /etc/pki/CA |
2.1.2 CA签发自身公钥
1 | [root@localhost CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 3650 |
信息可以随便填写,但后面生成LDAP证书的时候需要和这里的信息保持一致
2.1.3 创建index.txt和serial文件
index.txt 文件用于存放客户端证书信息,serial 文件用于存放客户端证书编号,可以自定义,用于识别客户端证书
1 | [root@localhost CA]# touch serial index.txt |
2.1.4 使用openssl命令获取证书信息
1 | [root@localhost CA]# openssl x509 -noout -text -in /etc/pki/CA/cacert.pem |
2.2 生成 LDAP 证书
2.2.1 获取LDAP证书
1 | [root@localhost CA]# mkdir /etc/openldap/ssl |
生成服务端密钥
1 | [root@localhost ssl]# openssl genrsa -out ldapkey.pem 2048 |
服务端向CA中心申请证书签署请求,相关信息必须和CA所填写一致才可以正常签发
1 | [root@localhost ssl]# openssl req -new -key ldapkey.pem -out ldap.csr -days 3650 |
2.2.2 生成LDAP证书
CA检测用户请求,通过后生成证书
1 | [root@localhost ssl]# openssl ca -in ldap.csr -out ldapcert.pem -days 3650 |
2.2.3 验证证书
成功生成证书后,可以 openssl 验证服务端证书的合法性
1 | [root@localhost ssl]# openssl verify -CAfile /etc/pki/CA/cacert.pem /etc/openldap/ssl/ldapcert.pem |
2.2.4 准备证书文件
后面ldap开启SSL需要使用到cacert.pem,ldapcert.pem,ldapkey.pem
1 | [root@localhost ssl]# cp /etc/pki/CA/cacert.pem /etc/openldap/ssl/ |
三、OpenLDAP 开启 TLS
3.1 自建 OpenLDAP
这里以我之前手动部署了一个openldap 2.4.44为例,开启TLS,不需要重新生成数据直接开启TLS认证就行
3.1.1 创建TLS的ldif配置文件
1 | [root@localhost schema]# vim enable_tls.ldif |
3.1.2 导入ssl配置
1 | [root@localhost schema]# ldapmodify -Y EXTERNAL -H ldapi:/// -D "cn=admin,dc=sys,dc=com" -w Abc.123456 -f enable_tls.ldif |
3.1.3 配置只开启ldaps安全端口
1 | [root@localhost schema]# vim /etc/sysconfig/slapd |
3.1.4 重启slapd服务
1 | [root@localhost schema]# systemctl restart slapd |
已经开启了636端口
3.1.5 测试连接
1 | #命令行连接需要开启 |
可以正常连接ldap,说明配置成功了
同时也可以测试当前套接字是否能通过CA的验证
1 | [root@localhost schema]# openssl s_client -connect 192.168.126.145:636 -showcerts -state -CAfile /etc/openldap/ssl/cacert.pem |
3.2 容器 OpenLDAP
为了节省资源现在很多服务都采用容器方式部署,OpenLDAP也不例可以使用容器运行,这里以2.6.3为例,镜像使用的bitnami/openldap 目前只有这个OpenLDAP镜像在长期更新
OpenLDAP 2.5版本开始支持很多新功能,像多重身份认证,密码过期提醒等,更多信息可前往官网查看
3.2.1 创建 OpenLDAP pvc
1 | [ec2-user@localhost ldap2.6]$ vim openldap-pvc.yaml |
注意:根据自己的环境修改storageClassName:存储类名称
3.2.2 导入 OpenLDAP 证书
将生成的OpenLDAP证书导入到k8s的secret中
1 | [ec2-user@localhost ssl]$ kubectl create secret generic openldap-certs -nmonitor --from-file=./cacert.pem --from-file=./ldapcert.pem --from-file=./ldapkey.pem |
3.2.3 创建 OpenLDAP deployment
1 | [ec2-user@localhost ldap2.6]$ vim openldap-deployment.yaml |
3.2.4 创建 OpenLDAP service
1 | [ec2-user@localhost ldap2.6]$ cat openldap-svc.yaml |
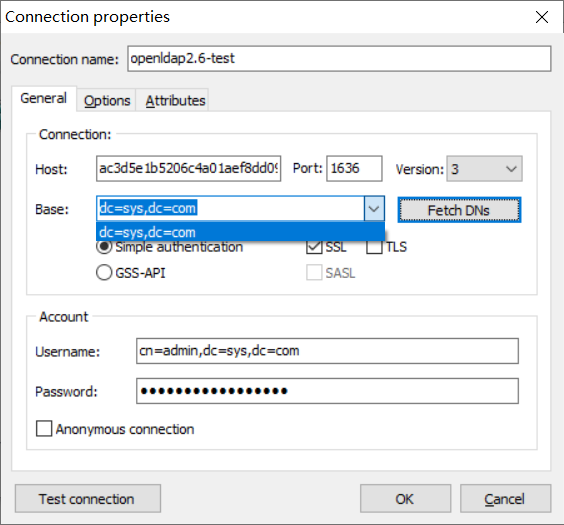
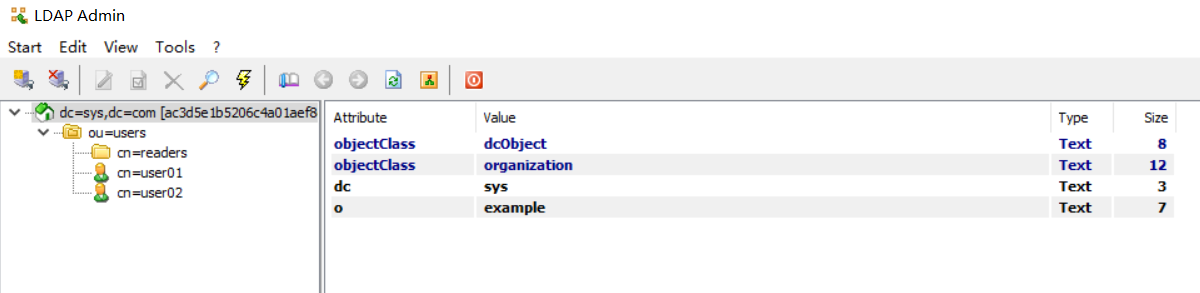
3.2.5 测试连接
这里使用ldapadmin连接