一、前言
通常我们会遵循专机专用的原则,单独使用一台服务器运行OpenLDAP,但实际使用到的资源只有几百兆甚至更少,存在一定的资源浪费,而且多出一台服务器也增加了一定的管理成本。这时如果在k8s容器中运行OpenLDAP的话,就能很好的解决这一问题。
二、部署 OpenLDAP 容器服务
2.1 创建 PVC
1 | [ec2-user@ip- ldap]$ cat openldap-pvc.yaml |
这里使用到了 storageClassName 储存类,可以参照各云厂商创建或自建存储类
2.2 创建 deployment
1 | [ec2-user@ip- ldap]$ cat openldap-deployment.yaml |
这里使用的镜像
osixia/openldap:1.5.0对应 OpenLDAP: slapd 2.4.57 版本
另外需要注意env里面配置的参数记得做修改
2.3 创建 svc
1 | [ec2-user@ip- ldap]$ cat openldap-svc.yaml |
service.beta.kubernetes.io/load-balancer-source-ranges:是AWS中对Network Load Balancer资源的白名单配置,参见:https://kubernetes-sigs.github.io/aws-load-balancer-controller/v2.4/guide/service/annotations/#access-control
至此,openldap服务就已经部署好了;接下来部署 phpldapadmin 页面用来管理openldap,使用客户端ldap管理工具的话可以跳过下面步骤
三、部署 phpldap 管理 OpenLDAP
3.1 创建 phpldap deploy,svc
1 | [ec2-user@ip- ldap]$ cat openldap-phpldapadmin.yaml |
3.2 创建 ingress 代理
1 | [ec2-user@ip- ldap]$ cat phpldapadmin-ingress.yaml |
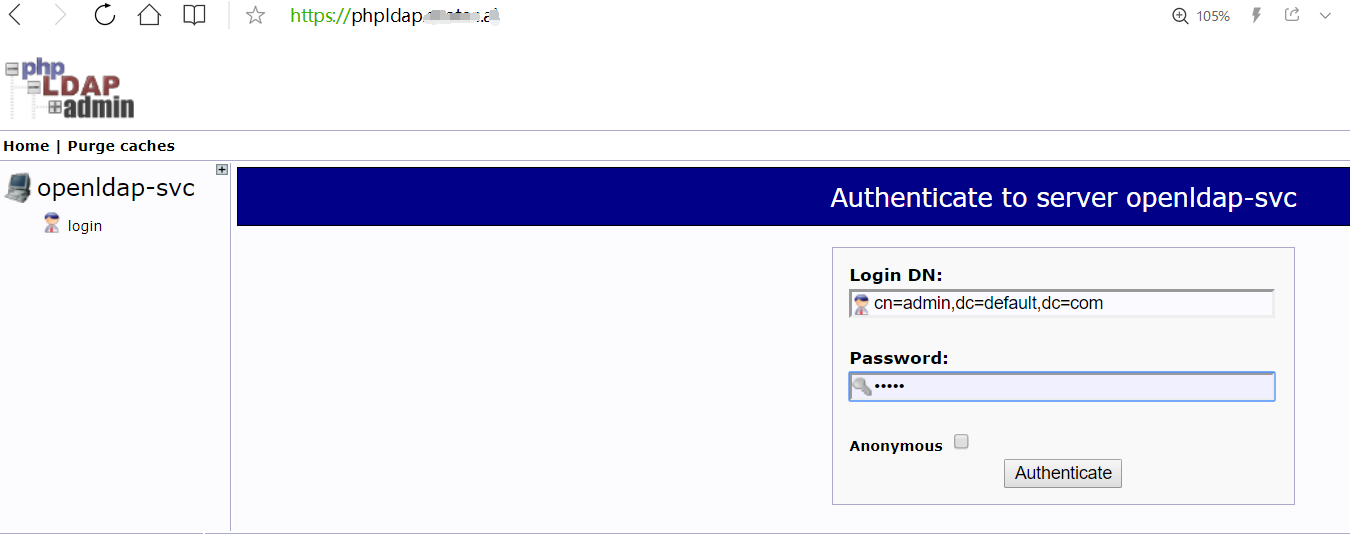
3.3 访问 phpldapadmin
login DN: cn=admin,dc=xxx,dc=com
Password: 系统变量中的:LDAP_ADMIN_PASSWORD
顺利登录后就可以通过web页面对openldap进行管理了
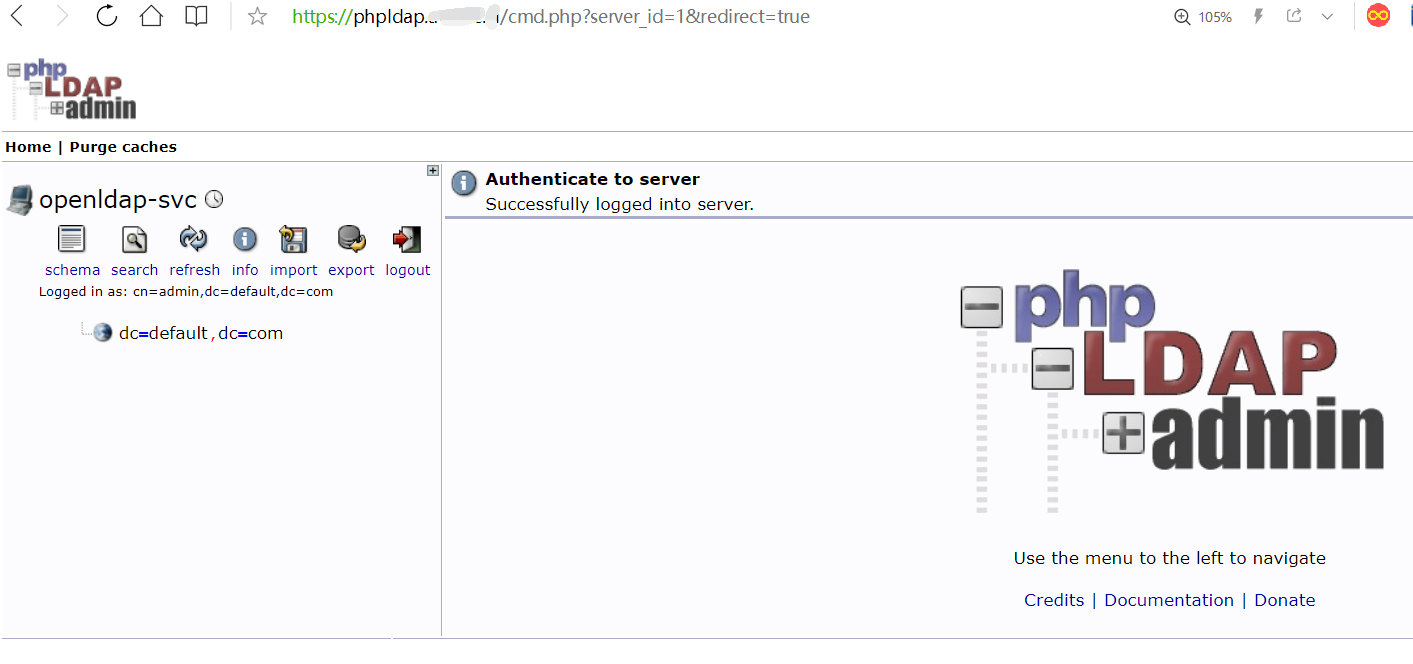
这里在登录时还有个小插曲,上面我设置的ldap密码使用了特殊字符在web登录时认证失败,但我通过ldap客户端工具是可以登录的,后来把ldap密码中的特殊字符&换掉就能顺利登录了