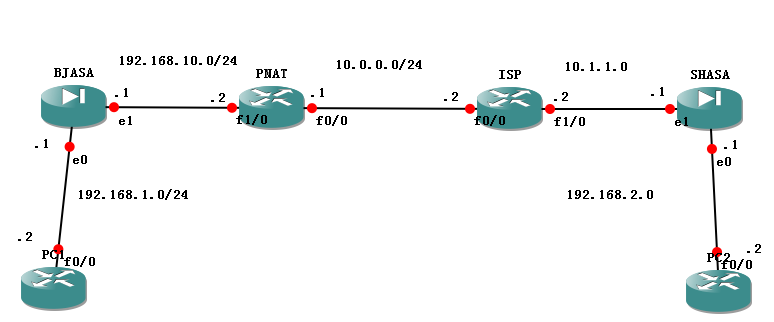
1、配置VPN连接
1.1 PC1配置
1 | PC1>en |
1.2 PC2配置
1 | PC2>en |
1.3 PNAT配置
1 | PNAT>en |
1.4 ISP配置
1 | ISP>en |
1.5 BJASA配置
1 | ciscoasa> en |
1.6 SHASA配置
1 | ciscoasa> en |
2、验证
前面我们在PNAT上开户了debug调试功能,主要测试如下:
2.1 在PC1上telnet PNAT,查看PNAT上的调试信息
在PC上telnet PNAT:
1 | PC1#telnet 192.168.10.2 |
在PNAT上查看调试信息:
1 | PNAT# |
因为前面配置的感兴趣流是192.168.1.0到192.168.2.0的,所以当PC1 telnet PNAT时不会走VPN遂道。
2.2 在PC1上ping 192.168.2.2,并查看PNAT上的调试信息
在PC1上ping 192.168.2.2:
1 | PC1#ping 192.168.2.2 source 192.168.1.2 repeat 10 |
在PNAT上查看调试信息:
1 | PNAT# |
可以看到PNAT上的地址转换还是跟前面看到的一样,这时我们配置的VPN就起作用了,因为192.168.1.0和192.168.2.0的通信都是在遂道里进行的,这里看不到他们的真实地址。
再查看BJASA连接状态:
1 | ciscoasa# show crypto isakmp sa |
可以看到状态是活跃的
查看数年连接的细节信息:
1 | ciscoasa# show crypto ipsec sa |