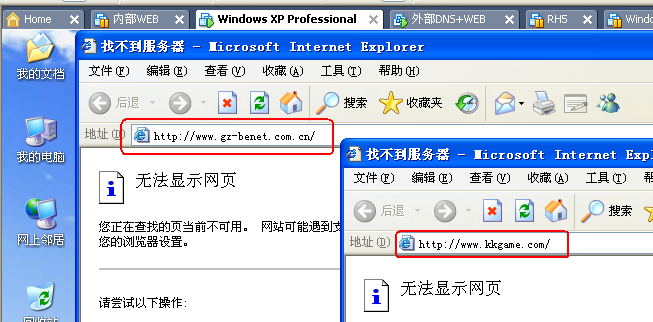
1、实验目的:
熟悉 ASA 安全配置—过滤 URL
2、实验环境和需求
- 在WEB上建立站点,配置DNS
- 在ASA上配置过滤特定的URL地
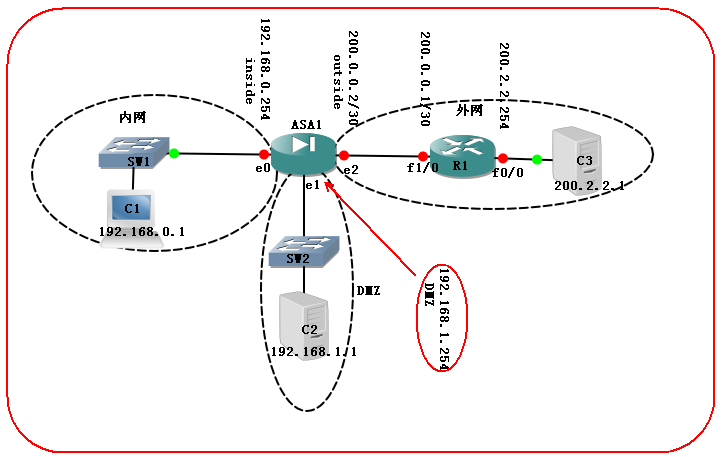
3、实验拓扑图
4、配置步聚
4.1基本配置
见上篇 Cisco ASA 防火墙基本配置
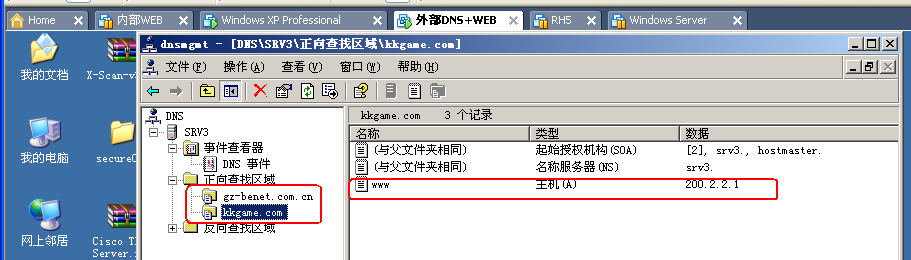
4.2 在外部服务器上建好 WEB 站点,并配置 DNS 新建两个区域
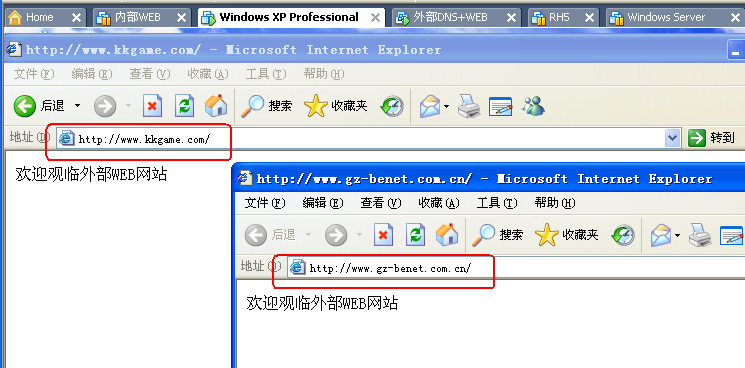
4.3 在内部PC上测试能通过www.gz-benet.com.cn和www.kkgame.com 访问外部服器的WEB 站点
4.4 在ASA上配置过滤 *.kkgame.com
1 | conf t |
4.5 在内部PC上测试
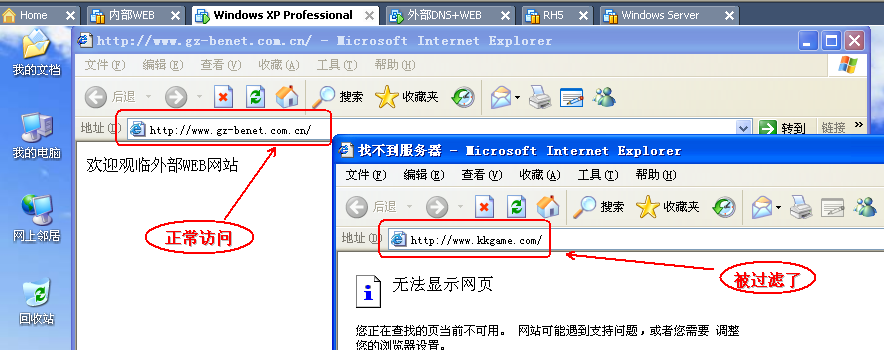
4.6 如果要过滤多个 URL 地址
1 | conf t |
4.7 在 PC 上测试,两个地址都不能访问了